We’re excited to announce some feature updates that are now available with PrinterLogic. Check out what’s new in serverless printing:
Secure Release Printing Updates
- New Ricoh and Fuji Xerox printer support. We recently launched new CPAs for Ricoh and Fuji. The Gen 2 CPA for Ricoh means SaaS now supports the manufacturer’s MP-series printers. In addition, we now support the ApeosPort series of Fuji Xerox printers (more than 60 models).
- New Control Panel Application (CPA) Manager. SaaS and the Virtual Appliance now include a new CPA Manager tool that’s found on your Service Client object on the Printer Apps tab. The CPA Manager is a quick way to get status or help troubleshoot all CPA installations in your environment. It allows up to 250 printer app installations or reconfigurations in batch mode. More information can be found in the CPA Manager topic in our documentation.
Identity (IdP) Update
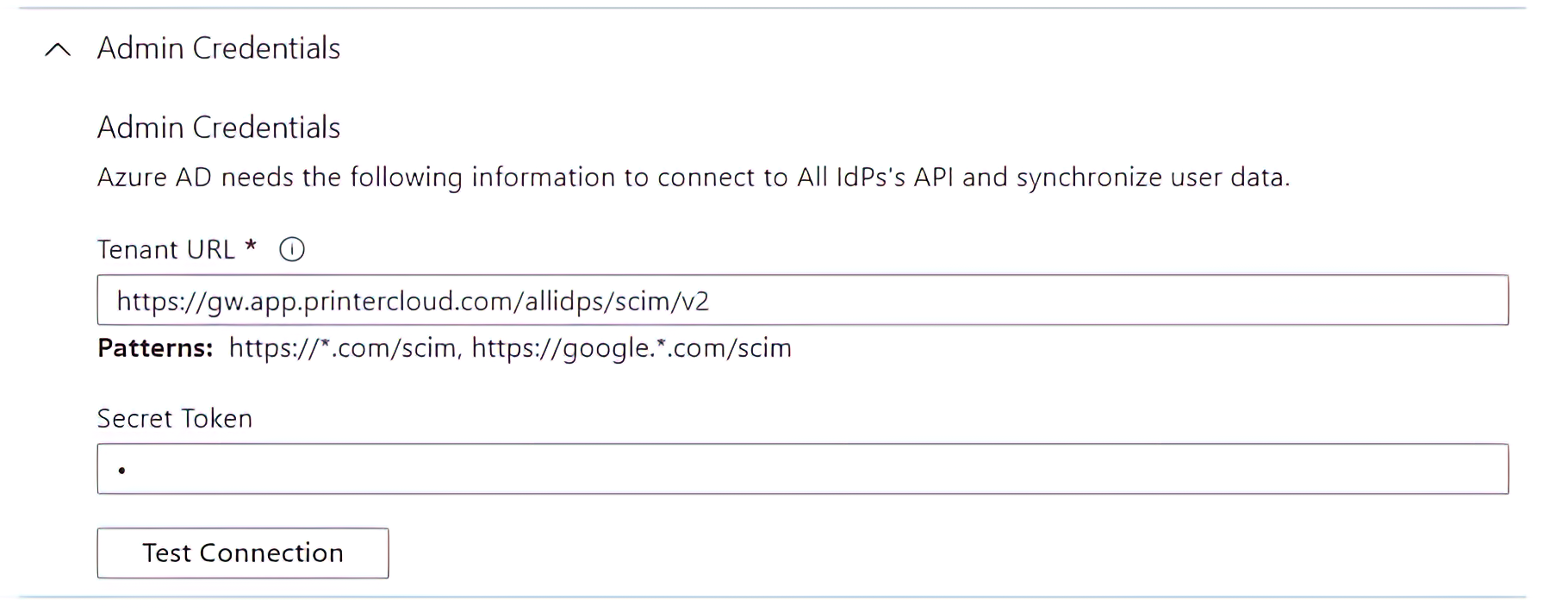
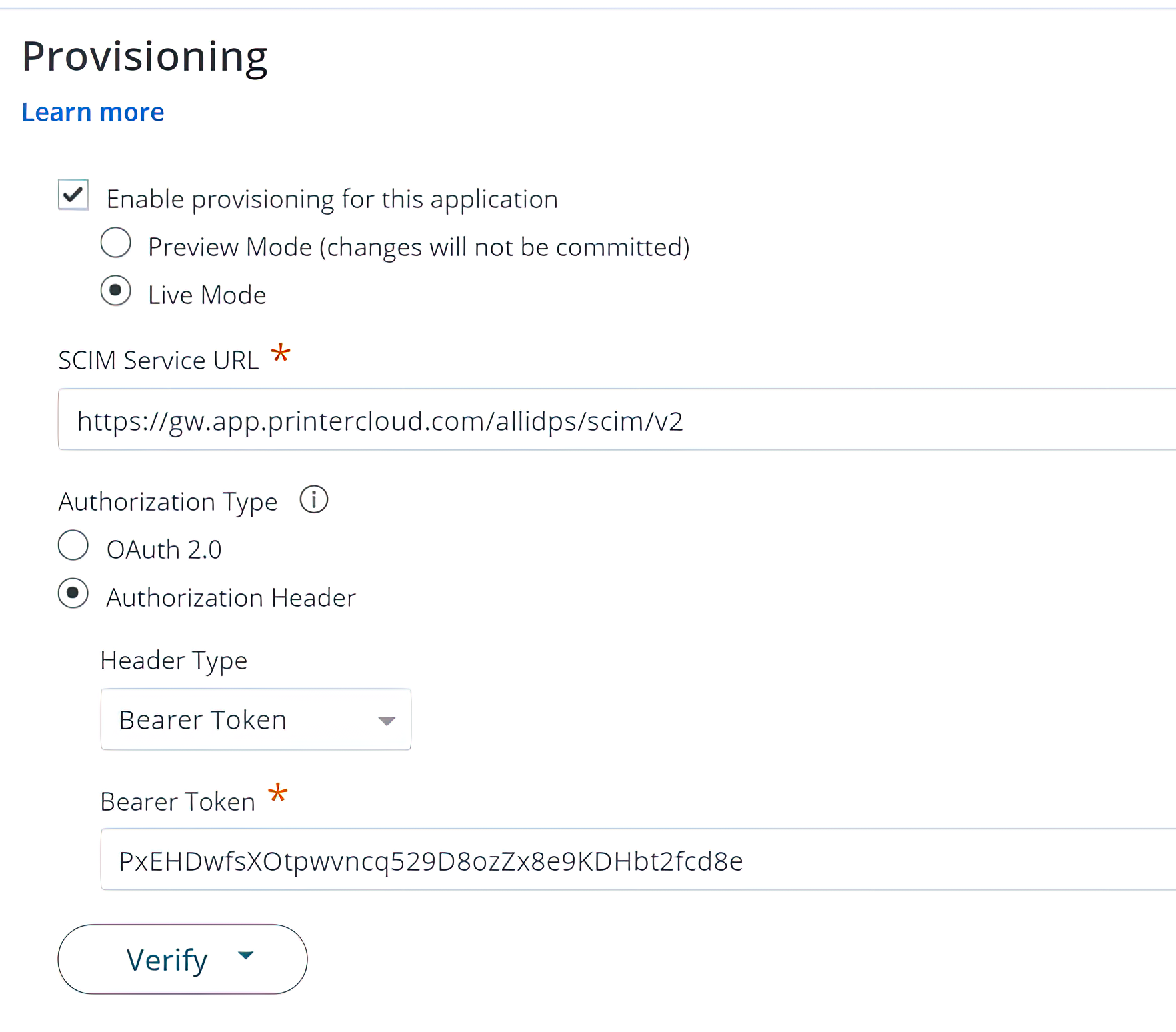
Concurrent IdP support now in production. As part of our new Advanced Security Bundle, multiple IdPs can be configured and enabled simultaneously. This is especially helpful when bringing a new acquisition into the organization. New workgroups can be merged into the organization’s print environment even if the new acquisition uses a different IdP.
Mobile App Updates
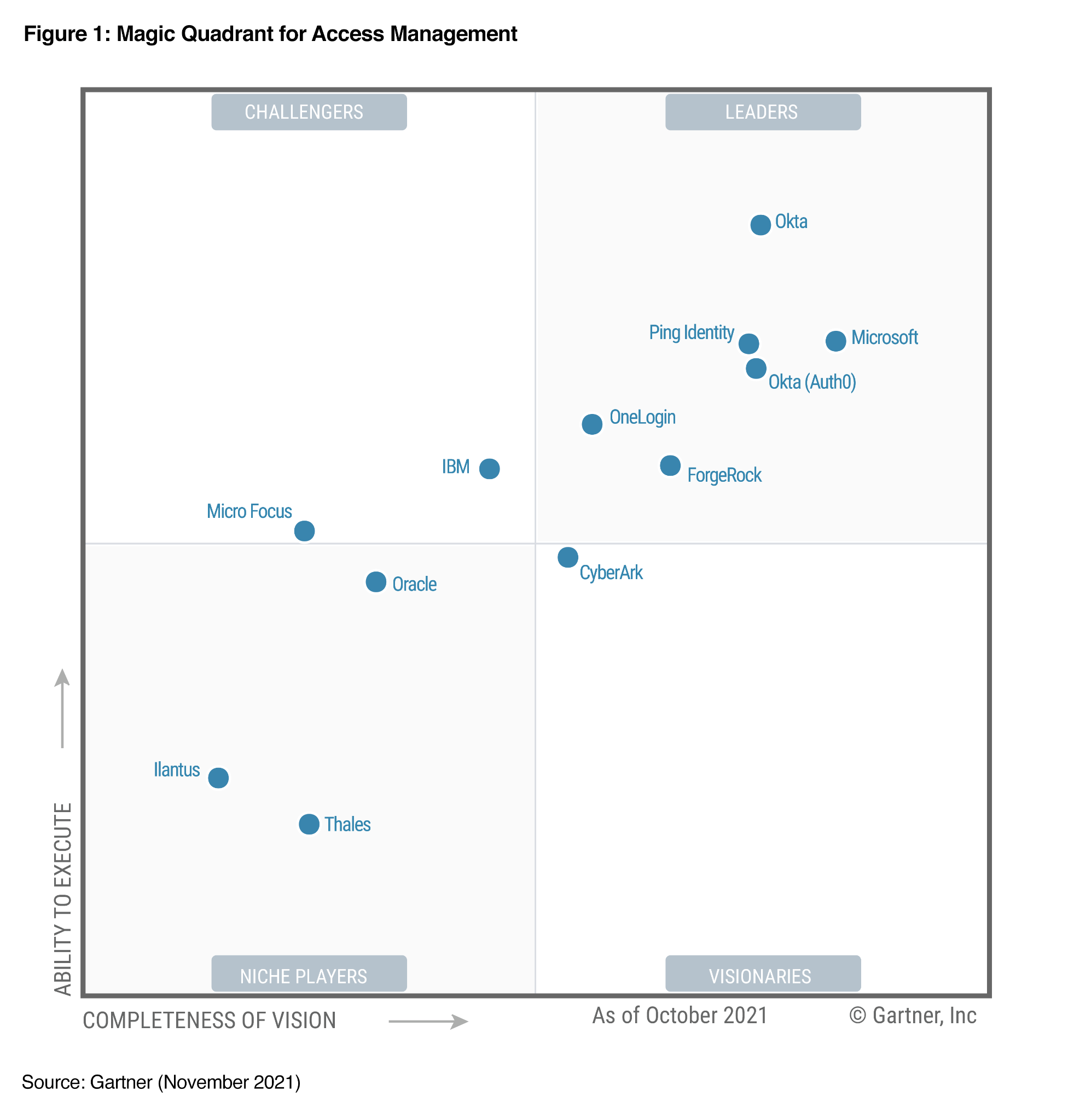
- Full suite of IdPs now supported. Our PrinterLogic App for iOS and Android now supports the same IdPs that are available within our SaaS platform. The roster now incorporates 10 providers, including Ping One, Ping Federate, CyberArk (formerly Idaptive), JumpCloud, OneLogin, ForgeRock, Google Identity, and more.
- Enhanced Mobile Device Manager (MDM) support. App deployments now include preconfiguring the customer’s PrinterLogic instance URL. This simplifies the sign-in process for the end user and reduces help-desk calls.
Virtual Appliance Updates
- Security vulnerability fix now available in VA Host update (1.0.742). Recently, an out-of-bounds vulnerability assigned to CVE-2021-44142 was disclosed in Samba versions prior to 4.13.17. This has been remediated. PrinterLogic VA customers with host versions 1.0.735 and earlier should update their VA Host, which includes the latest application release as well. Release notes and associated files can be found here.
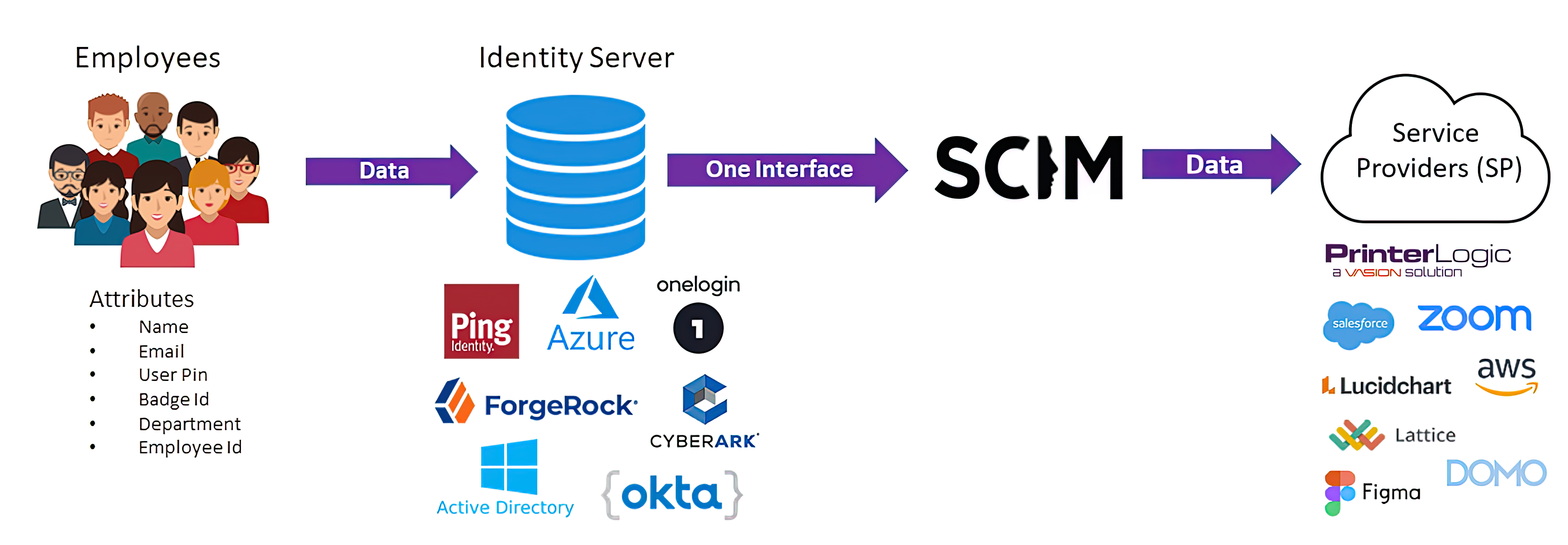
- Just in Time (JIT) provisioning for IdP-managed Badge/PIN and more. We know that for Virtual Appliance customers, JIT provisioning is preferred to SCIM. With that in mind, we just expanded the list of user attributes that can be provisioned, including authPin, authPinUser, badge, manager, department, and job title—if they are configured in the IdP. This means you can take advantage of IdP-managed badge and PIN, a feature that was only available in SCIM apps previously.
Advanced Reporting Update
Enterprise Data Warehouse (EDW) now available in PrinterLogic SaaS and the VA. The EDW feature facilitates data mining using your own Business Intelligence (BI) tools. The feature lets business analysts create custom reports for resources managed by PrinterLogic, including print jobs in a specific time frame filtered by printer type, region, paper type, black/white vs. color, etc. It supports standard BI tools such as Crystal Reports, Domo, Tableau, and more.
To learn more about these feature updates or our full PrinterLogic feature set, contact our customer support team.