PrinterLogic is pleased to announce the release of an all-new Control Panel Application (CPA) for select FS, TASKalfa, and ECOSYS series multifunction printers from Kyocera. The introduction brings to 10 the total number of MFP brands supported by our SaaS and Virtual Appliance platforms for secure printing.
The Kyocera CPA follows our recent announcement of the PrinterLogic Fuji Xerox CPA and will come as equally welcome news to customers in the European and Asia-Pacific regions, where Kyocera is especially popular.
The PrinterLogic app installs directly on the printer and provides a flexible secure-printing experience for IT administrators and end users alike. PrinterLogic’s Kyocera CPA will work with any printer running Java VM version 1.4 subset and above—including models such as the FS C8525MFP, TASKalfa 6052ci, and ECOSYS M3540idn.
You can view the full list of supported models here.
The PrinterLogic Kyocera CPA is built entirely on our second-generation CPA platform, which leverages the rich capabilities of our cloud-native SaaS printing solution to provide a more seamless and more secure experience across multiple printer models and brands. Kyocera vetted and approved the CPA prior to release.

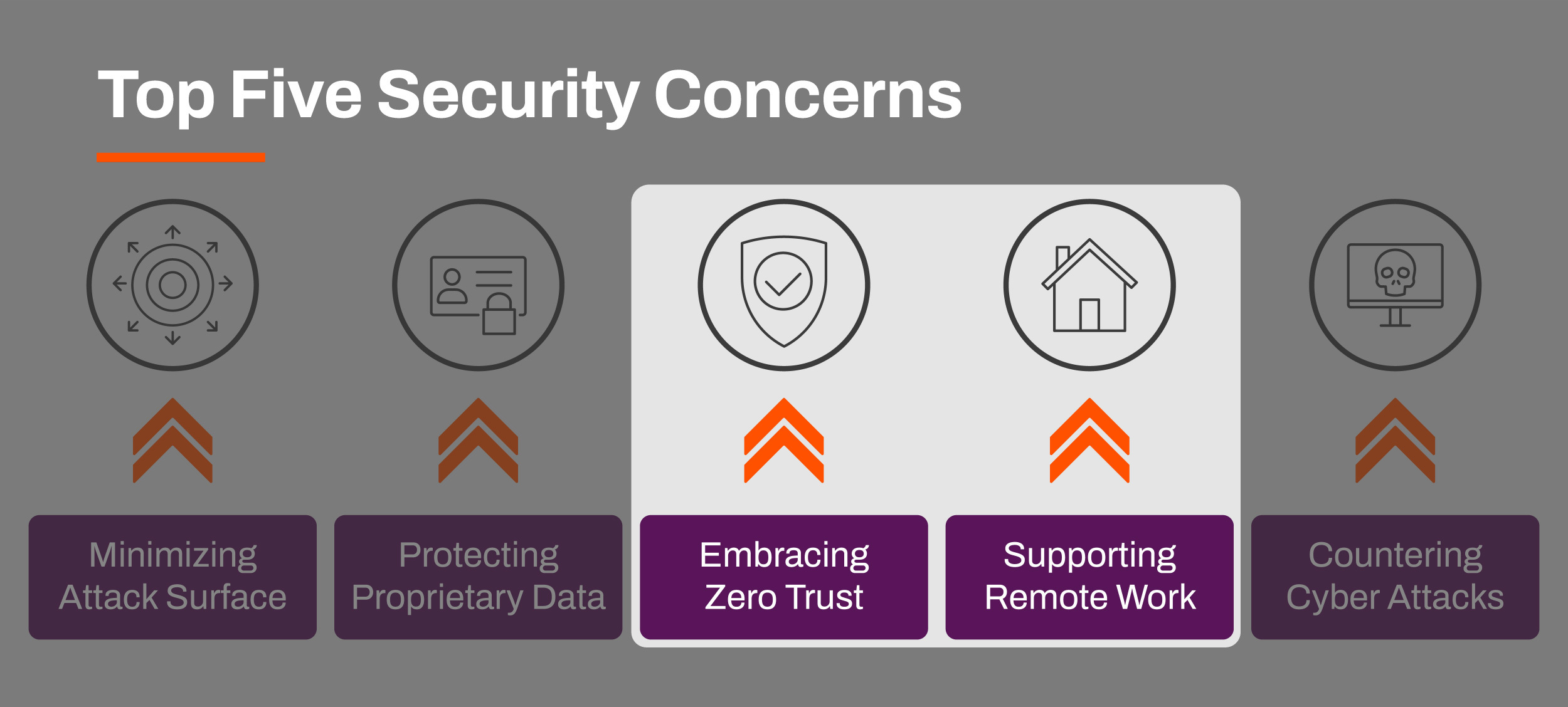
New Advanced Security Bundle supports 90+ percent of the commercial MFP market
With this addition, PrinterLogic’s SaaS and Virtual Appliance platforms now support ten major network printer brands, representing well over 90 percent of the commercial multifunction printer market. Secure Release Printing is available as part of the PrinterLogic Advanced Security Bundle, introduced in January.
Secure Release Printing—also known as pull printing or “follow me” printing—ensures that the user who initiates the print job is physically standing at the printer before the output appears in the tray. This approach helps protect confidential information and reduces waste caused by redundant or abandoned print jobs.
New app uses PrinterLogic’s latest SSO and IdP support technology
The new CPA employs core PrinterLogic technology that supports Single Sign-On (SSO) protocols. Users authenticate one time to access any app or function on that printer. Once the user authenticates on the printer, PrinterLogic’s app employs a “listener” mode and allows them to release held documents without signing in again.
The new app features an intuitive touchscreen interface that gives users four choices for proving their identity. These include badge swipe, smartphone release with QR code support, UserID/PIN, and conventional Username/Password login credentials. PrinterLogic supports Microsoft Active Directory and leading cloud-based Identity Providers (IdPs) such as Okta, Azure AD, Google Identity, Ping, and more.
How it works: Secure Release Printing workflow for users
Once network printers are configured for either pull printing or secure printing, the user workflow proceeds as follows:
- First, a user prints from their workstation as usual, and the print job is held securely on the workstation until the user goes to the printer to retrieve it.
- At the printer, the user swipes their badge or authenticates using any of the available methods. All held print jobs appear on the printer’s screen. Users simply pick the job or jobs they want to print. Or, users can delete jobs they no longer care about.
- With the pull-printing option, a universal driver is used. That means users can decide which printer they want to use after initiating the print job.
Secure printing ensures that confidential documents get into the right hands and aren’t left sitting on a printer tray to tempt prying eyes. In addition, these methods do away with abandoned print jobs and wasted consumables. For more details, see our Secure Release Printing feature page.
In addition to secure printing, PrinterLogic offers many other security features:
- PrinterLogic eliminates print servers, each of which is a repository for thousands of confidential documents and is vulnerable to an attack.
- PrinterLogic has passed the AWS Well-Architected Review and inherits all of the benefits of AWS Cloud Security.
- PrinterLogic uses centrally-managed direct IP printing to keep jobs local. Printing continues even if your internet connection goes down.
- PrinterLogic automatically logs document name, print source, print destination, and authenticated username for audit tracking and data-loss prevention.
- PrinterLogic’s architecture complies with strict U.S. government standards (FIPS 140-2, with 140-3 compliance pending).
- PrinterLogic supports multifactor authentication, including CAC/PIV-enabled release printing on any network printer.
A true SaaS solution that eliminates all print-related infrastructure
Unlike some “cloud-optimized” print management software, PrinterLogic is a true, multi-tenant SaaS offering. It’s not a cloud-hosted shortcut that leaves you stuck with server licensing, configuration, and maintenance. Automatic updates ensure you have the most current and reliable solution possible—backed by a guaranteed service-level agreement.